For years, American aerospace industry has allegedly been infiltrated by a shadowy group of hackers believed to be affiliated with Chinese military. US space industry’s trading partners have also not been spared by this group, revealed a US-based cyber security company CrowdStrike.
CrowdStrike officials have declared People’s Liberation Army 12 bureau’s unit 61486 based in Shanghai responsible for attacking American and numerous other western networks. These cyber-assaults date back to as far as 2007. CrowdStrike states that this group has managed to target communication, space, and aerospace sectors through “popular productivity applications such as Adobe Reader and Microsoft Office to deploy custom malware through targeted email attacks,” reported Reuters.
The list of accusations has been outlined in a 62 page report published by CrowdStrike on Monday which involves blames like phishing emails and using Trojan horse document. This group, informally known as Putter Panda, conducts forensic investigations for clients enduring offensive security violations. For instance, whenever a target clicks on a specific document or downloads it, they can easily take over their entire computer. This power is then used by the hackers for stealing housing blueprints, serves, list of clients and other highly sensitive data, reported Ars Technica.
Researchers have acknowledged that “Putter Panda is a determined adversary group, conducting intelligence-gathering operations targeting the Government, Defense, Research, and Technology sectors in the United States, with specific targeting of the US Defense and European satellite and aerospace industries. The PLA’s GSD Third Department is generally acknowledged to be China’s premier Signals Intelligence (SIGINT) collection and analysis agency, and the 12th Bureau Unit 61486, headquartered in Shanghai, supports China’s space surveillance network.”
CrowdStrike published this report to show how deep-rooted this problem is. The report arrived just three weeks after the surprise move from US Justice Department of impeaching People’s Liberation Army hacker unit’s five members. They were accused of stealing US trade secrets.
Chinese spokespersons denied the legitimacy of the Department’s assertions on the basis that the US National Security agency has already launched such attacks.
Jiang Jun, an official representative for the state Internet Information Office informed pro-government Xinhua News Agency: “For a long time, governments and enterprises of a few countries have gathered sensitive information on a large scale, taking advantage of their monopoly in the market and technological edge. They not only seriously undermine the interests of their clients but also threaten cyber security of other countries.”
Jun’s response provoked Dmitri Alperovitch, co-founder CrowdStrike who also authorized disclosure of this report on Monday, to access US intelligence and Justice Department officials for consultation.
“After the Chinese response, where they basically said this is all fabricated, we said why don’t we unleash something that’s undeniable,” Alperovitch informed Reuters.
The post Chinese military hacked U.S. aerospace industry for seven years: Report appeared first on Hack Read.

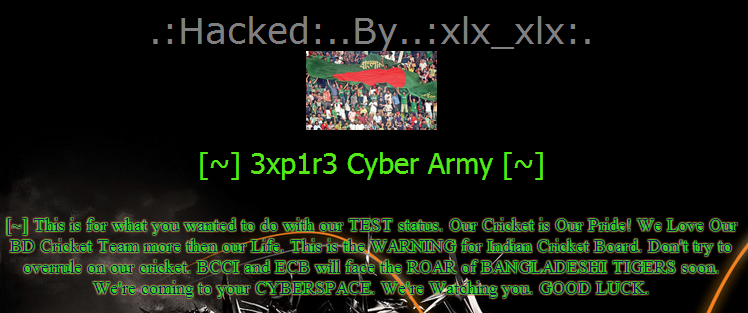
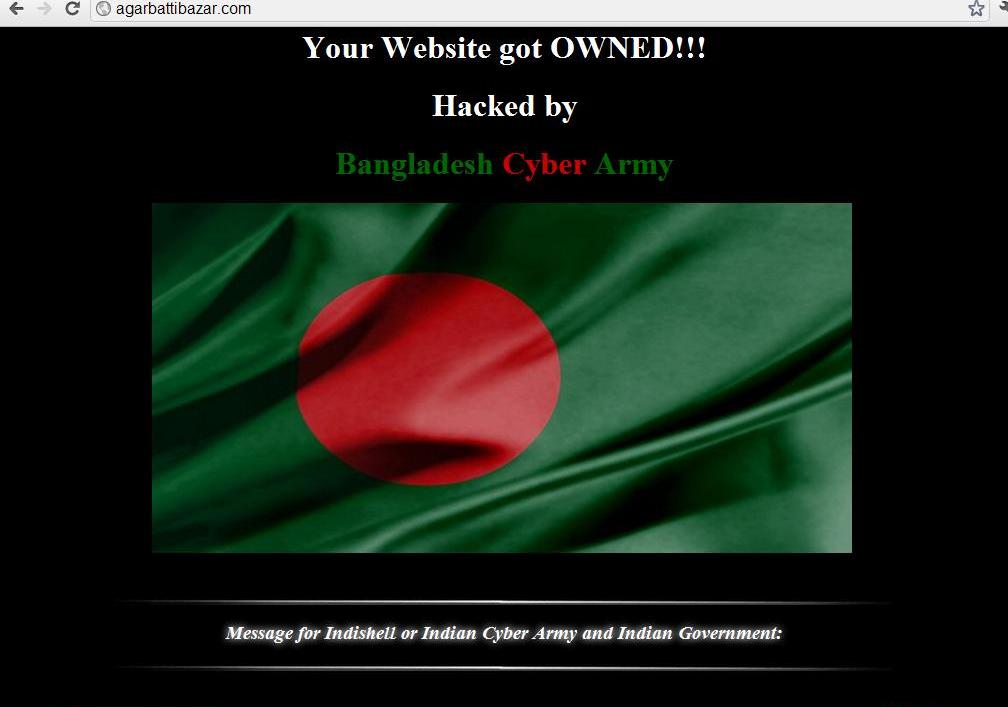
 According to Ash3ll, a member of indishell, these hacks are reply to Bangladeshi Hacker's #OP-INDIA which was started on 09th feb 2012 when a youtube video containing a warning message from Bangladeshi black hat hackers [BBHH] to the Indian Government for their alleged crimes against humanity and specially against Bangladeshis.
[video w="500" h="300"]http://www.youtube.com/watch?v=eAyx6V5JHi8[/video]
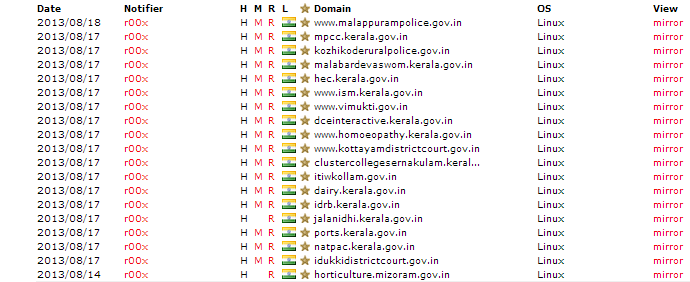
Mirrors of hacked Websites:
List of hacked website Defaced Sites
http://www.moef.gov.bd/
http://www.mincom.gov.bd/
http://www.cga.gov.bd/
http://www.mopme.gov.bd/
http://www.rdcd.gov.bd/
http://www.moysports.gov.bd/
http://www.mole.gov.bd/
http://www.bfri.gov.bd/
http://www.moind.gov.bd/
http://www.mopt.gov.bd/
http://www.lgd.gov.bd/
http://www.minlaw.gov.bd/
http://www.dmrd.gov.bd/
http://www.nlaso.gov.bd/
http://www.ictd.gov.bd/
http://www.cddl.gov.bd/
http://www.mosict.gov.bd/
http://www.gaziwires.gov.bd/
http://www.boiler.gov.bd/
http://www.bcsadminacademy.gov.bd/
http://www.lawjusticediv.gov.bd/
http://www.moedu.gov.bd/
http://www.guchhogram.gov.bd/
http://www.cca.gov.bd/
http://www.nmst.gov.bd/
http://www.legislativediv.gov.bd/
http://www.etl.gov.bd/
http://www.latc.gov.bd/
http://www.drr.gov.bd/
http://www.bnnssddhk.org.bd/
http://www.msw.gov.bd/
http://www.bffwt.org.bd/
http://www.molwa.gov.bd/
http://www.fd.gov.bd/
http://banglabazar24.com/
http://cmchorthosurgery.edu.bd/
http://domicilelivingbd.com/
http://www.newsctg24.com/
http://ad.dainikazadi.net/
http://azadijobs.com/
http://college.dainikazadi.net/
http://dainikazadi.org/
http://epaper.dainikazadi.net/
http://mdc.dainikazadi.net/
http://probashi.dainikazadi.net/
http://www.dainikazadi.org/
http://attendance.azaditechnologies.com/
http://softbd.com/images/
http://softbd.info/images/
http://southern.edu.bd/images/
http://bloodbank.azaditechnologies.com/
http://cmp.azaditechnologies.com/
http://ctgclub.azaditechnologies.com/
http://edainikazadi.azaditechnologies.com/
http://hrm.azaditechnologies.com/
http://igmisbd.azaditechnologies.com/
http://khansourcing.azaditechnologies.com/
http://kkautomobiles.azaditechnologies.com/
http://module.azaditechnologies.com/
http://mostafa1.azaditechnologies.com/
http://mostafa2.azaditechnologies.com/
http://mostafa3.azaditechnologies.com/
http://mostafa4.azaditechnologies.com/
http://personal.azaditechnologies.com/
http://phplist.azaditechnologies.com/
http://probashi.azaditechnologies.com/
http://azaditechnologies.com/
http://nhldc.gov.bd/
http://www.ulabdu.edu.bd/
http://cdvs.ac.bd/
http://nhldc.gov.bd/
http://www.ulabdu.edu.bd/
http://cdvs.ac.bd/
http://www.apsb.org.bd/
http://bsl.gov.bd/
http://ccr.gov.bd/
http://www.freelancer.com.bd/
http://theroysfashion.com/
Destroyed Sites
list of Bangladesh GOV site freezed by Godzilla aka GOD
Proof:
http://3.bp.blogspot.com/-A7RSlsw4W7U/TzZl-OOMgqI/AAAAAAAACN8/ZfAgIrlTtHc/s1600/Godzilla.jpg
dshe.gov.bd
fourm.dshe.gov.bd
www.fireservice.gov.bd
www.mha.gov.bd
www.police.gov.bd
www.brta.gov.bd
www.coastguard.gov.bd
www.macademy.gov.bd
www.natpdae.gov.bd
www.parjatan.gov.bd
www.jmba.gov.bd
www.visitbangladesh.gov.bd
www.bsbk.gov.bd
www.urbanvolunteer-fscd.gov.bd
www.bsl.gov.bd
www.vgdupdwa.gov.bd
www.atomic.sparrso.gov.bd
www.wmip-bwdb.gov.bd
www.perp.gov.bd
www.cairo.mofa.gov.bd
www.vacancies.lgd.gov.bd
www.jmba.gov.bd
fltc.gov.bd
cmmu.gov.bd
rcc.gov.bd
pep.gov.bd
unior.sparrso.gov.bd
dot.gov.bd
dcrangpur.gov.bd
dcbarisal.gov.bd
dcmadaripur.gov.bd
ptkpolice.gov.bd
e-card.sparrso.gov.bd
madrid.mofa.gov.bd
molwa.gov.bd
alatetanasoli.lgd.gov.bd
rdcd.gov.bd
bpsc.gov.bd
arash.sparrso.gov.bd
bbs.gov.bd
dcjhalakathi.gov.bd
institutes.lgd.gov.bd
manila.mofa.gov.bd
lged.gov.bd
esiraj.gov.bd
tv.kgdcl.gov.bd
pbs.reb.gov.bd
tv.mpl.gov.bd
tv.archaeology.gov.bd
pers.coastguard.gov.bd
tg.archaeology.gov.bd
test.aap.gov.bd
db.chilmariuzp.gov.bd
us.nape.gov.bd
wahv.mha.gov.bd
bbs.gov.bd
a2i.pmo.gov.bd
seedwingmoa.gov.bd
dlib.biwtc.gov.bd
bangladeshmuseum.gov.bd
bpsc.gov.bd
gb.biwtc.gov.bd
bpsc.gov.bd
cmmu.gov.bd
biwtc.gov.bd
chilmariuzp.gov.bd
namdec.gov.bd
mofiz.emrd.gov.bd
myphone.bttb.gov.bd
hms2.hajj.gov.bd
hms31.hajj.gov.bd
admin.bangladeshmuseum.gov.bd
ubsbd.com.bd
aslgroup.com.bd
businesschancebd.com
connectbd.net
dl.brta.gov.bd
dscebd.org
ibnsinapharma.com
justiciars.com
kenabecha.com.bd
laveilabaya.com
mtbcap.com
mtbsecurities.com
muslimaidbd.org
popibd.org
popidream.org
sportsreporter24.com
www.afmcbd.com
www.amazon.com
www.bpatc.org.bd
www.bup.edu.bd
www.campaign.com.bd
www.connectbd.com
www.ibnsinapharma.com
www.jce-ieb.org
www.jpi.edu.bd
www.kenabecha.com.bd
www.ksb.org.bd
According to Ash3ll, a member of indishell, these hacks are reply to Bangladeshi Hacker's #OP-INDIA which was started on 09th feb 2012 when a youtube video containing a warning message from Bangladeshi black hat hackers [BBHH] to the Indian Government for their alleged crimes against humanity and specially against Bangladeshis.
[video w="500" h="300"]http://www.youtube.com/watch?v=eAyx6V5JHi8[/video]
Mirrors of hacked Websites:
List of hacked website Defaced Sites
http://www.moef.gov.bd/
http://www.mincom.gov.bd/
http://www.cga.gov.bd/
http://www.mopme.gov.bd/
http://www.rdcd.gov.bd/
http://www.moysports.gov.bd/
http://www.mole.gov.bd/
http://www.bfri.gov.bd/
http://www.moind.gov.bd/
http://www.mopt.gov.bd/
http://www.lgd.gov.bd/
http://www.minlaw.gov.bd/
http://www.dmrd.gov.bd/
http://www.nlaso.gov.bd/
http://www.ictd.gov.bd/
http://www.cddl.gov.bd/
http://www.mosict.gov.bd/
http://www.gaziwires.gov.bd/
http://www.boiler.gov.bd/
http://www.bcsadminacademy.gov.bd/
http://www.lawjusticediv.gov.bd/
http://www.moedu.gov.bd/
http://www.guchhogram.gov.bd/
http://www.cca.gov.bd/
http://www.nmst.gov.bd/
http://www.legislativediv.gov.bd/
http://www.etl.gov.bd/
http://www.latc.gov.bd/
http://www.drr.gov.bd/
http://www.bnnssddhk.org.bd/
http://www.msw.gov.bd/
http://www.bffwt.org.bd/
http://www.molwa.gov.bd/
http://www.fd.gov.bd/
http://banglabazar24.com/
http://cmchorthosurgery.edu.bd/
http://domicilelivingbd.com/
http://www.newsctg24.com/
http://ad.dainikazadi.net/
http://azadijobs.com/
http://college.dainikazadi.net/
http://dainikazadi.org/
http://epaper.dainikazadi.net/
http://mdc.dainikazadi.net/
http://probashi.dainikazadi.net/
http://www.dainikazadi.org/
http://attendance.azaditechnologies.com/
http://softbd.com/images/
http://softbd.info/images/
http://southern.edu.bd/images/
http://bloodbank.azaditechnologies.com/
http://cmp.azaditechnologies.com/
http://ctgclub.azaditechnologies.com/
http://edainikazadi.azaditechnologies.com/
http://hrm.azaditechnologies.com/
http://igmisbd.azaditechnologies.com/
http://khansourcing.azaditechnologies.com/
http://kkautomobiles.azaditechnologies.com/
http://module.azaditechnologies.com/
http://mostafa1.azaditechnologies.com/
http://mostafa2.azaditechnologies.com/
http://mostafa3.azaditechnologies.com/
http://mostafa4.azaditechnologies.com/
http://personal.azaditechnologies.com/
http://phplist.azaditechnologies.com/
http://probashi.azaditechnologies.com/
http://azaditechnologies.com/
http://nhldc.gov.bd/
http://www.ulabdu.edu.bd/
http://cdvs.ac.bd/
http://nhldc.gov.bd/
http://www.ulabdu.edu.bd/
http://cdvs.ac.bd/
http://www.apsb.org.bd/
http://bsl.gov.bd/
http://ccr.gov.bd/
http://www.freelancer.com.bd/
http://theroysfashion.com/
Destroyed Sites
list of Bangladesh GOV site freezed by Godzilla aka GOD
Proof:
http://3.bp.blogspot.com/-A7RSlsw4W7U/TzZl-OOMgqI/AAAAAAAACN8/ZfAgIrlTtHc/s1600/Godzilla.jpg
dshe.gov.bd
fourm.dshe.gov.bd
www.fireservice.gov.bd
www.mha.gov.bd
www.police.gov.bd
www.brta.gov.bd
www.coastguard.gov.bd
www.macademy.gov.bd
www.natpdae.gov.bd
www.parjatan.gov.bd
www.jmba.gov.bd
www.visitbangladesh.gov.bd
www.bsbk.gov.bd
www.urbanvolunteer-fscd.gov.bd
www.bsl.gov.bd
www.vgdupdwa.gov.bd
www.atomic.sparrso.gov.bd
www.wmip-bwdb.gov.bd
www.perp.gov.bd
www.cairo.mofa.gov.bd
www.vacancies.lgd.gov.bd
www.jmba.gov.bd
fltc.gov.bd
cmmu.gov.bd
rcc.gov.bd
pep.gov.bd
unior.sparrso.gov.bd
dot.gov.bd
dcrangpur.gov.bd
dcbarisal.gov.bd
dcmadaripur.gov.bd
ptkpolice.gov.bd
e-card.sparrso.gov.bd
madrid.mofa.gov.bd
molwa.gov.bd
alatetanasoli.lgd.gov.bd
rdcd.gov.bd
bpsc.gov.bd
arash.sparrso.gov.bd
bbs.gov.bd
dcjhalakathi.gov.bd
institutes.lgd.gov.bd
manila.mofa.gov.bd
lged.gov.bd
esiraj.gov.bd
tv.kgdcl.gov.bd
pbs.reb.gov.bd
tv.mpl.gov.bd
tv.archaeology.gov.bd
pers.coastguard.gov.bd
tg.archaeology.gov.bd
test.aap.gov.bd
db.chilmariuzp.gov.bd
us.nape.gov.bd
wahv.mha.gov.bd
bbs.gov.bd
a2i.pmo.gov.bd
seedwingmoa.gov.bd
dlib.biwtc.gov.bd
bangladeshmuseum.gov.bd
bpsc.gov.bd
gb.biwtc.gov.bd
bpsc.gov.bd
cmmu.gov.bd
biwtc.gov.bd
chilmariuzp.gov.bd
namdec.gov.bd
mofiz.emrd.gov.bd
myphone.bttb.gov.bd
hms2.hajj.gov.bd
hms31.hajj.gov.bd
admin.bangladeshmuseum.gov.bd
ubsbd.com.bd
aslgroup.com.bd
businesschancebd.com
connectbd.net
dl.brta.gov.bd
dscebd.org
ibnsinapharma.com
justiciars.com
kenabecha.com.bd
laveilabaya.com
mtbcap.com
mtbsecurities.com
muslimaidbd.org
popibd.org
popidream.org
sportsreporter24.com
www.afmcbd.com
www.amazon.com
www.bpatc.org.bd
www.bup.edu.bd
www.campaign.com.bd
www.connectbd.com
www.ibnsinapharma.com
www.jce-ieb.org
www.jpi.edu.bd
www.kenabecha.com.bd
www.ksb.org.bd


 IAS100 is an Online portal for UPSC IAS, Indian Civil Service exam preparation and various various other state service examinations.
Hackers have discributed credential details in four parts that can be obtained from following links:
IAS100 is an Online portal for UPSC IAS, Indian Civil Service exam preparation and various various other state service examinations.
Hackers have discributed credential details in four parts that can be obtained from following links:
 Hacked website belongs to the Finance Department Batagram, which is under the Government of Khyber Pakhtunkhwa deals with the subjects pertaining to finance of the District Government and financial matters affecting the District as a whole, preparation of annual budget statements and supplementary/excess budget statements for the consideration of the district accounts and audits of the District Government Organization.
Hacked website belongs to the Finance Department Batagram, which is under the Government of Khyber Pakhtunkhwa deals with the subjects pertaining to finance of the District Government and financial matters affecting the District as a whole, preparation of annual budget statements and supplementary/excess budget statements for the consideration of the district accounts and audits of the District Government Organization.